screenshot courtesy of /u/JakeSteam
How do I revoke access to this worm?
There is an emerging Reddit thread about this issue that may contain more up-to-date information as the situation develops: https://www.reddit.com/r/google/comments/692cr4/new_google_docs_phishing_scam_almost_undetectable/
Per Reddit user JakeSteam, take the following steps:
- Revoke access to “Google Docs” immediately. The real one doesn’t need access.
- Try and see if your account has sent any spam emails, and send a followup email linking to this post / with your own advice if so.
- Inform whoever sent you the email about the spam emails, and that their account is compromised.
What data has been compromised?
If you authorized the fake “Google Docs” application, an unknown attacker may have access to the following:
- Ability to manage your contacts (read/write)
- Ability to read, send, delete, and manage your email
In theory, this means it is possible everyone affected has had their entire inbox scraped for passwords or other credentials. While this cannot be ruled out since the application gained full access to Gmail, I personally believe this to be unlikely. This was a fast-moving worm and some Gmail users have many gigabytes of mail stored. To scrape all of this mail would greatly slow down the spread of this worm, since the malicious server would be spending time exfiltrating data, not propagating.
Just because it is unlikely all your mail has been stolen doesn’t mean it hasn’t been. I would encourage rekeying any systems with credentials stored in your mailbox.
What is https://googledocs.g-cloud.pro/g.php and how did I authorize it?
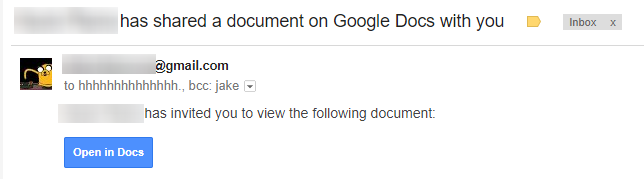
You may have received an email like the following – a near-perfect imitation of the real Google Docs sharing notification. If you clicked on “Open in Docs” and proceeded to authenticate, your Gmail account may be compromised.
This phishing email uses OAuth and a convincing bait email to get access to your emails and address book, then send more phishing on your behalf.
The initial phishing email was sent to the address “[email protected]” and would Bcc the target. It included a link like this:
hxxps://accounts.google.com/o/oauth2/auth?client_id=346348828325-vlpb3e70lp89pd823qrcb9jfsmu556t8.apps.googleusercontent.com&scope=https%3A%2F%2Fmail.google.com%2F+https%3A%2F%2Fwww.googleapis.com%2Fauth%2Fcontacts&immediate=false&include_granted_scopes=true&response_type=token&redirect_uri=https%3A%2F%2Fgoogledocs.g-cloud.pro%2Fg.php&customparam=customparam
This authorizes 346348828325-vlpb3e70lp89pd823qrcb9jfsmu556t8.apps.googleusercontent.com (since pulled offline) to access the OAuth scopes https://mail.google.com and https://www.googleapis.com/auth/contacts. The victim is then redirected to https://googledocs.g-cloud.pro/g.php. This script uses the newly-gained access to send more phishing emails to all your contacts.
What’s going on at that @mailinator.com account?
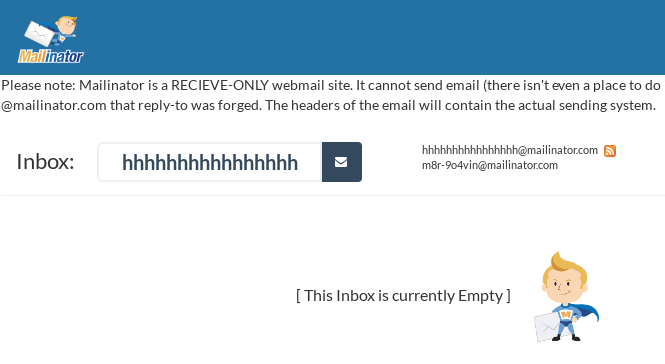
As of 4:18PM EST it looks like Mailinator has intervened and disabled this inbox. While this is a bummer for researchers like myself, it is a relief they have taken the time to prevent further disclosure of emails affected by this phishing attack.
It is worth noting they’ve added the following disclosure to their site, likely in response to the attacker’s use of their service.
Please note: Mailinator is a RECIEVE-ONLY webmail site. It cannot send email (there isn’t even a place to do it on the site). If you received an email “from” @mailinator.com that reply-to was forged. The headers of the email will contain the actual sending system.
Additional domains the attack utilized
The following domains were also utilized in this attack:
googledocs[.]docscloud.download
googledocs[.]docscloud.info
googledocs[.]docscloud.win
googledocs[.]g-cloud.pro
googledocs[.]g-cloud.win
googledocs[.]g-docs.pro
googledocs[.]g-docs.win
googledocs[.]gdocs.download
googledocs[.]gdocs.pro
googledocs[.]gdocs.win
source: https://www.cyberscoop.com/gmail-phishing-attack-oauth/